- A+
所属分类:linux技术
nginx访问控制,用户认证,配置https,zabbix监控nginx状态页面
nginx访问控制
用于location段
allow:设定允许哪台或哪些主机访问,多个参数间用空格隔开
deny: 设定禁止哪台或哪些主机访问,多个参数间用空格隔开
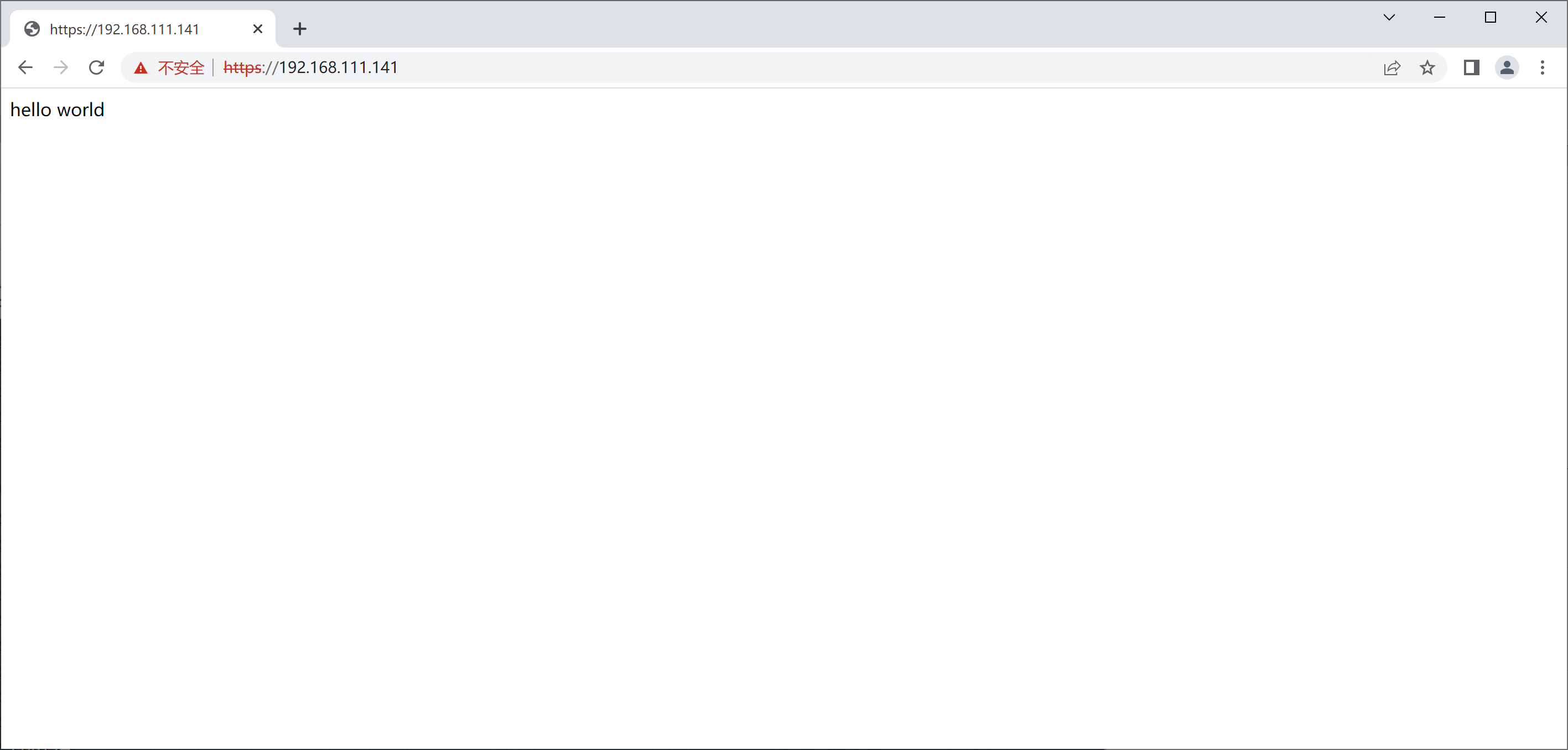
//测试 [root@nginx ~]# cd /usr/local/nginx/html/ [root@nginx html]# ls 50x.html index.html [root@nginx html]# echo 'hello world' > index.html [root@nginx html]# systemctl restart nginx //虚拟机访问 [root@nginx html]# curl 192.168.111.141 hello world 访问测试
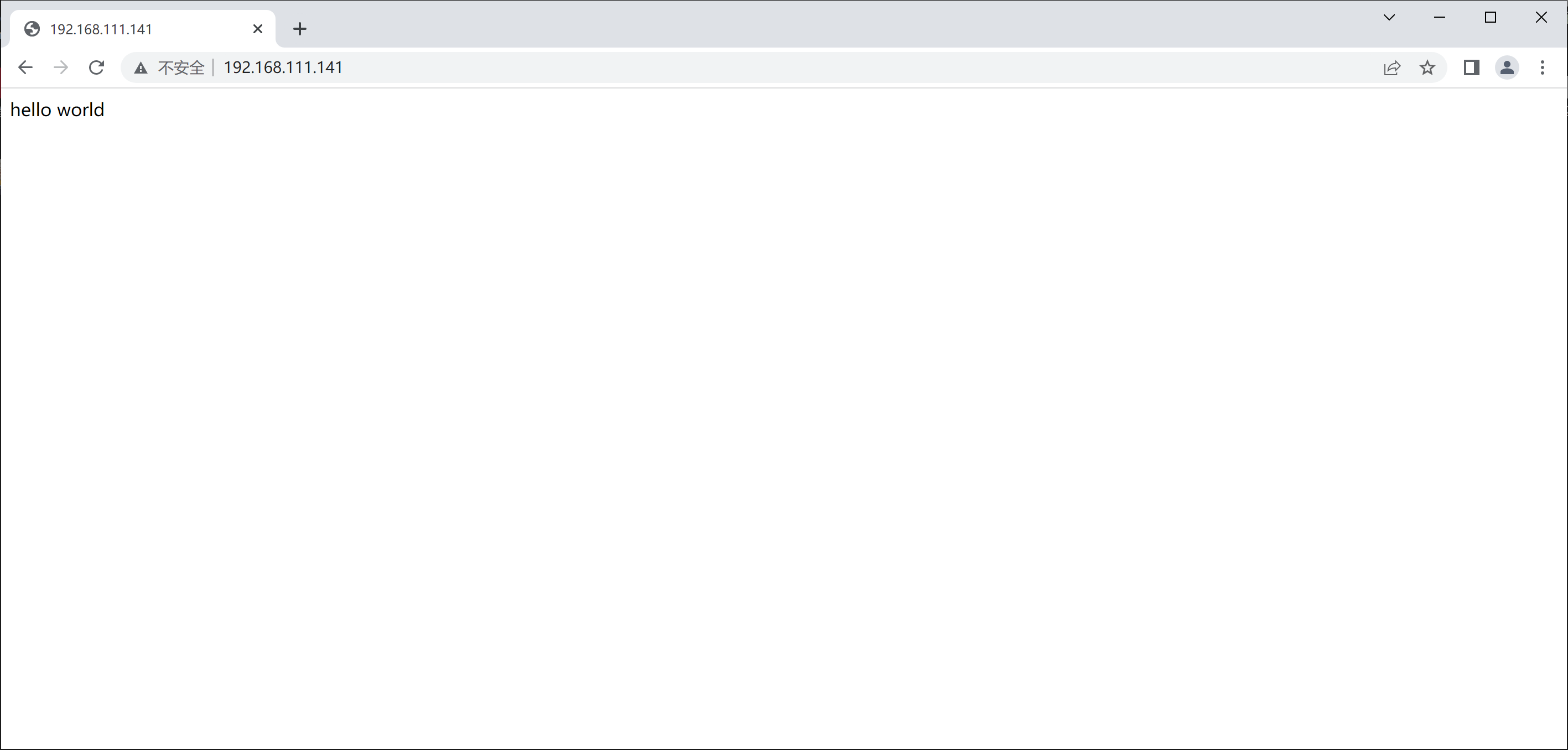
//修改配置文件 [root@nginx html]# cd .. [root@nginx nginx]# vim conf/nginx.conf location / { allow 192.168.111.141; deny all; root html; index index.html index.htm; } [root@nginx nginx]# systemctl restart nginx //虚拟机访问 [root@nginx nginx]# curl 192.168.111.141 hello world 访问测试

nginx用户认证
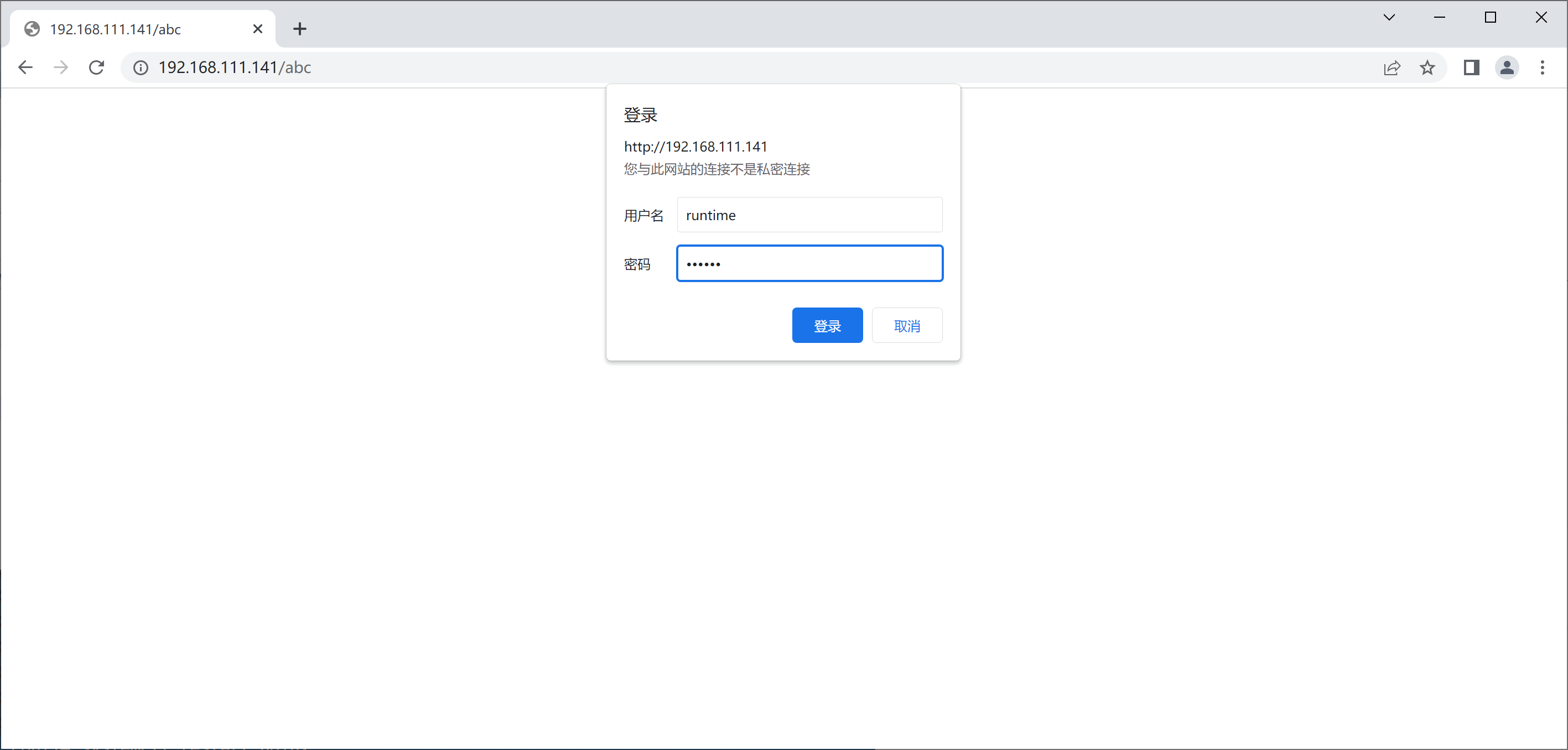
//安装httpd工具包 [root@nginx ~]# yum -y install httpd-tools //修改配置文件 [root@nginx ~]# cd /usr/local/nginx/conf/ [root@nginx conf]# vim nginx.conf location / { root html; index index.html index.htm; } location /abc { auth_basic "ABC"; auth_basic_user_file "/usr/local/nginx/conf/.pass"; //密码位置 root html; index index.html; } //生成用户密码 [root@nginx conf]# htpasswd -cm /usr/local/nginx/conf/.pass runtime New password: Re-type new password: Adding password for user runtime [root@nginx conf]# cat .pass runtime:$apr1$nPzAshNM$nvmalzBcNQlagDB3ipABc1 //加密后的密码 [root@nginx conf]# systemctl restart nginx 直接访问
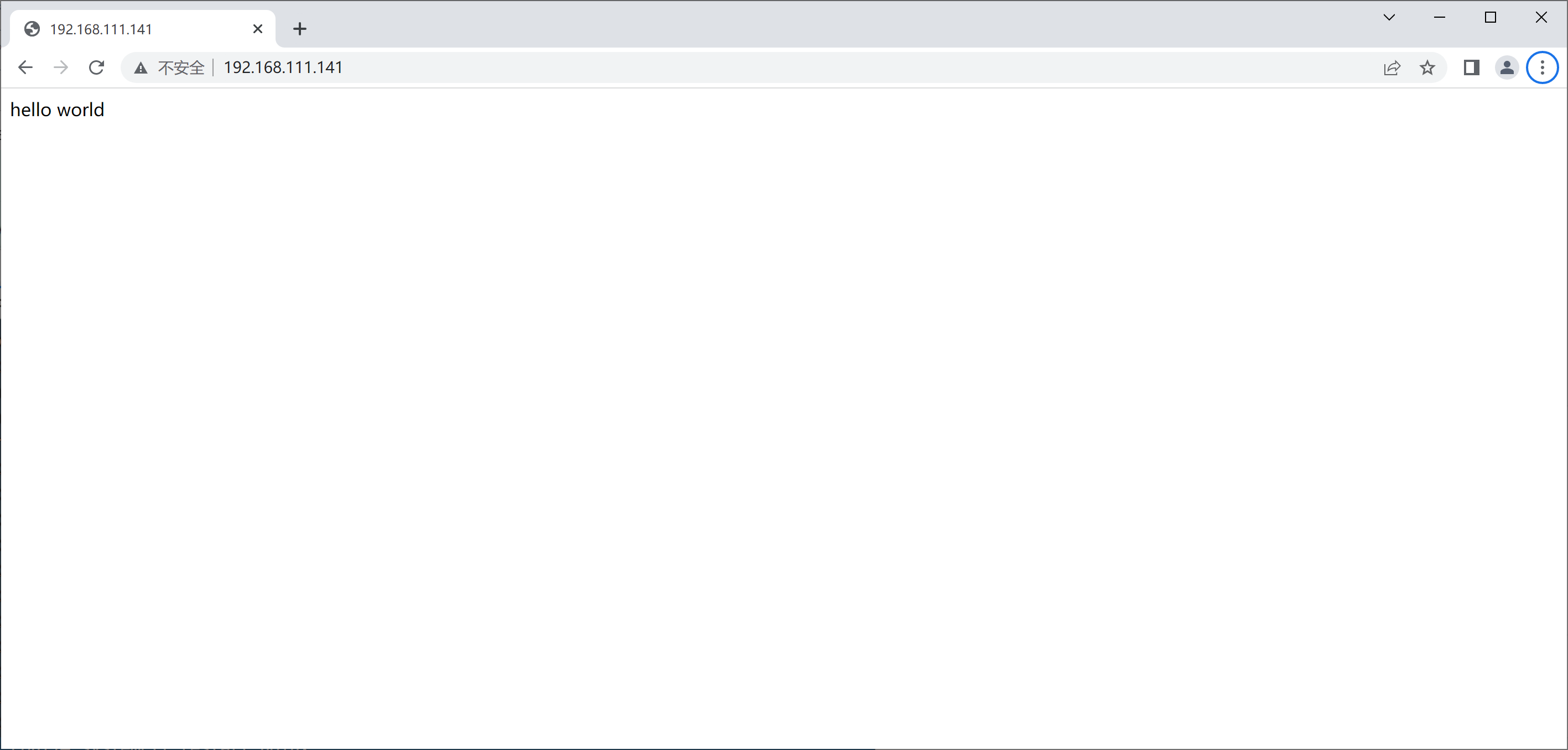
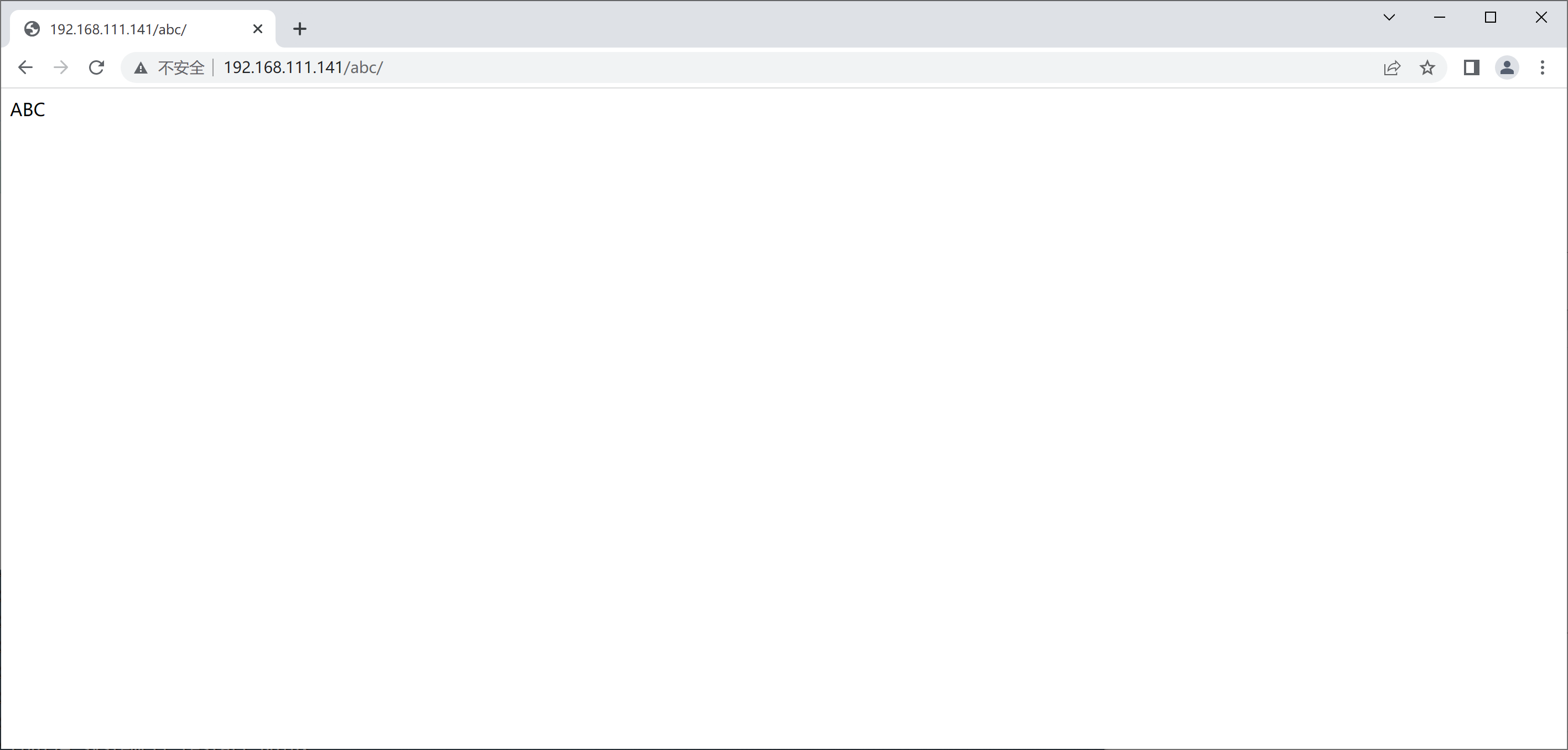
访问根下的abc
nginx配置https
证书申请及签署步骤
a) 生成申请请求 b) RA核验c) CA签署 d) 获取证书
//生成证书 [root@nginx ~]# cd /etc/pki/ [root@nginx pki]# mkdir CA [root@nginx pki]# cd CA/ [root@nginx CA]# mkdir private [root@nginx CA]# (umask 077;openssl genrsa -out private/cakey.pem 2048) //括号必须要 Generating RSA private key, 2048 bit long modulus (2 primes) ........+++++ ............................................................................+++++ e is 65537 (0x010001) [root@nginx CA]# ls private/ cakey.pem //CA生成自签署证书 [root@nginx CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 365 You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:CN //国家 State or Province Name (full name) []:HB //省份 Locality Name (eg, city) [Default City]:WH //市 Organization Name (eg, company) [Default Company Ltd]:TX Organizational Unit Name (eg, section) []:www.example.com //域名 Common Name (eg, your name or your server's hostname) []:www.example.com Email Address []:1@2.com [root@nginx CA]# mkdir certs newcerts crl [root@nginx CA]# touch index.txt && echo 01 > serial //生成密钥 [root@nginx CA]# cd /usr/local/nginx/conf/ [root@nginx conf]# mkdir ssl [root@nginx conf]# cd ssl [root@nginx ssl]# (umask 077;openssl genrsa -out nginx.key 2048) Generating RSA private key, 2048 bit long modulus (2 primes) ..................................................+++++ ..................................+++++ e is 65537 (0x010001) //证书签署请求 [root@nginx ssl]# openssl req -new -key nginx.key -days 365 -out nginx.csr Ignoring -days; not generating a certificate You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:HB Locality Name (eg, city) [Default City]:WH Organization Name (eg, company) [Default Company Ltd]:TX Organizational Unit Name (eg, section) []:www.example.com Common Name (eg, your name or your server's hostname) []:www.example.com Email Address []:1@2.com Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []: //签署证书 [root@nginx ssl]# openssl ca -in nginx.csr -out nginx.crt -days 365 Using configuration from /etc/pki/tls/openssl.cnf Check that the request matches the signature Signature ok Certificate Details: Serial Number: 1 (0x1) Validity Not Before: Oct 13 06:50:03 2022 GMT Not After : Oct 13 06:50:03 2023 GMT Subject: countryName = CN stateOrProvinceName = HB organizationName = www.example.com organizationalUnitName = www.example.com commonName = www.example.com emailAddress = 1@2.com X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Comment: OpenSSL Generated Certificate X509v3 Subject Key Identifier: DA:A8:6A:71:7F:86:76:C8:A2:99:C2:D4:D1:79:F9:43:95:4C:41:12 X509v3 Authority Key Identifier: keyid:DB:B7:F5:00:4D:A0:A3:A7:CB:D1:70:FE:B6:CD:71:D0:F1:55:AB:DC Certificate is to be certified until Oct 13 06:50:03 2023 GMT (365 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated [root@nginx ssl]# ls nginx.crt nginx.csr nginx.key //修改配置文件加入生成的密钥和证书 [root@nginx ssl]# cd .. [root@nginx conf]# vim nginx.conf //先取消注释 server { listen 443 ssl; server_name www.example.com; ssl_certificate /usr/local/nginx/conf/ssl/nginx.crt; //修改为密钥和证书的位置 ssl_certificate_key /usr/local/nginx/conf/ssl/nginx.key; ssl_session_cache shared:SSL:1m; ssl_session_timeout 5m; ssl_ciphers HIGH:!aNULL:!MD5; ssl_prefer_server_ciphers on; location / { root html; index index.html index.htm; } } } [root@nginx conf]# systemctl restart nginx